Three separate yet complementary reports on Intellexa and its Predator spyware were released today, unveiling the company’s operations within the global digital surveillance industry. Google Threat Intelligence, Amnesty International’s Security Lab, and Recorded Future each published new technical and operational findings on Intellexa’s methods. At the same time, the major joint investigation “Intellexa Leaks”—a collaboration between Greek inside story, Israel’s Haaretz, and Switzerland’s WAV Research Collective—was made public.
The Intellexa Leaks reveal materials leaked from the company between 2018 and 2025. Combined with forensic analysis by Amnesty International’s Security Lab, the documents expose new clients as well as long-standing ones that remain active.
The investigation also sheds light on the internal workings of the spyware firm. The leaked files allow past cyberattacks to be definitively attributed to Intellexa’s customers — including the attack targeting Greek journalist Thanasis Koukakis.
Most critically, the files show that in certain cases Intellexa retained the technical capability to remotely connect to its clients’ surveillance systems after installation and during routine operations.
Even if presented as technical support, such remote access raises significant legal concerns. If a spyware vendor can view data from ongoing state surveillance operations, it may be liable for illegal or abusive targeting.
The revelations come at a pivotal moment in Greece, where a criminal trial on unlawful interception of communications is underway. Four individuals — three with links to Intellexa — are facing charges.
On November 26, Haaretz asked Intellexa whether it had access to client systems, whether such access had been authorized, and whether technical limitations existed. On December 3, a lawyer representing Intellexa founder Tal Dilian replied that the company “has committed no crime and has not operated any cyber system in Greece or elsewhere.” The answer, however, did not address the core questions.
Despite numerous exposés, financial sanctions, and its ongoing legal case in Greece, Intellexa continues to operate and sell its products. Today’s journalistic revelations document an attempted infection of a human-rights lawyer’s phone in Pakistan during the summer of 2025 using Intellexa technology.
Meanwhile, Intellexa maintains access to cutting-edge zero-day exploits and continually expands its device-infection techniques. The most alarming development is the Aladdin system, which allows Predator to be installed simply by displaying a malicious advertisement—no click required.
The company’s apparent use of the global online advertising ecosystem to hack phones raises immediate questions of responsibility for the AdTech industry, long regarded as a “neutral” technical infrastructure.
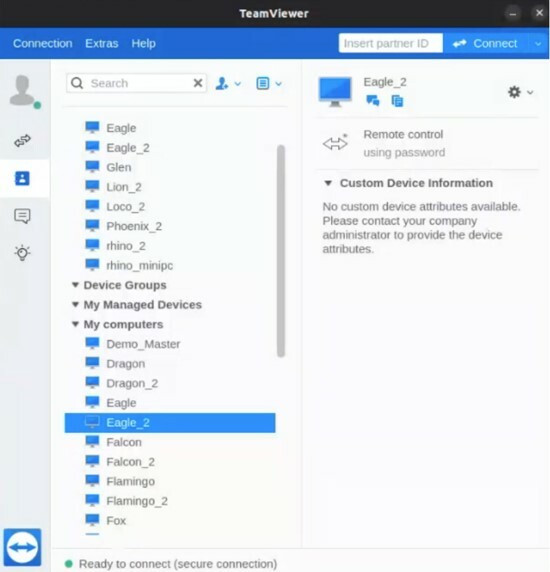
Videos and technical documents from the Intellexa Leaks show Predator in action. In a training video, a company instructor connects live to a customer system code-named EAGLE_2 and navigates data collected from victims.
The footage shows real-world infection attempts—including one in Kazakhstan, where the target’s IP and the attack process are recorded. Investigators also identify malicious domains disguised as “news websites” used to lure victims. Amnesty confirms these domains are part of the Predator infrastructure.
The leaks additionally detail Intellexa’s multi-method infection ecosystem: from traditional malicious links to tools that leverage telecom providers to inject malicious code into users’ traffic. The most dangerous remains the aforementioned Aladdin system.
Recorded Future’s report maps the global network of companies linked to Intellexa, revealing dozens of front firms across Europe, Africa, Asia, and the Middle East. These entities form a worldwide supply chain—ad-tech firms tied to Aladdin, logistics companies transporting equipment, tech firms hosting servers.
One example is PULSE FZCO in the United Arab Emirates, which shipped equipment to intelligence agencies in Botswana and a company in Kazakhstan—both countries where Predator operations later emerged.
Greece also appears in this network. According to Recorded Future, Athens served as a training hub for Predator operators, while Intellexa-connected companies remain at the center of the still-unfolding Predatorgate scandal.
Adding to the picture, Google’s Threat Intelligence Group confirmed that Intellexa is among the world’s most active users of zero-day exploits targeting mobile devices. Since 2021, Google has attributed at least 15 critical zero-days to the company.
In 2025, a newly detected attack forced Google to issue an emergency security update and notify hundreds of potential victims worldwide. The company found that Intellexa’s malware had been installed on devices without any user interaction. The tool, dubbed PREYHUNTER, could record conversations, keystrokes, and images from the camera.
Due to the gravity of the situation, Google alerted governments and state agencies across multiple countries. It also sent hundreds of notifications to individuals targeted by Intellexa clients in nations including Pakistan, Kazakhstan, Egypt, Saudi Arabia, and others.
Google has now published its findings, blacklisted all malicious domains via Safe Browsing, and called on governments to strengthen protections and support global efforts to curb commercial spyware.
Taken together, the revelations show Intellexa not as a simple tech vendor but as a full-fledged surveillance ecosystem. It develops exploits, works with government agencies, moves specialized equipment around the world, infiltrates online advertising networks — and, most concerning of all, appears to retain access to the very surveillance systems it installs.